Branding Okta
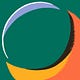
This weekend, I branded an Okta login screen for some client applications and resources that I’m writing. The result pairs a custom domain with branding assets and looks like this.
These styles are alternate views of the default pages that Okta provides. The theme and custom domain are not directly related to an Authorization Server or a client Application. That is, this is not multi-tenancy. All the brands will use the same account.
The branding that I focused on was the logo and the custom domain. Before I started working with the Okta configuration, I acquired
A subdomain (www.bekwam.biz) in this example,
An SSL certificate (CN=www.bekwam.biz), and
The marketing assets which were a PNG.
A subdomain is needed (bekwam.biz itself won’t work) because you’ll prepare a DNS CNAME record that will alias the custom subdomain (www.bekwam.com) to the Okta-provided one (something of the form okta-dev-12345678.okta.com).
You’ll also provide DNS CNAME records to alias email. This is so emails coming from Okta don’t use the default noreply@test-account.dev address. In my case, they will come from webmaster@bekwam.biz.
SSL Notes
Once you make the DNS adjustments, you’ll enter the SSL contents into Okta: private key, public key, and intermediate certificates. These are PEM-encoded files. I used Network Solutions and purchased a SSL Xpress with Domain Validation (~$80/yr). The validation step requires a reply from an email account based on the domain (webmaster@bekwam.biz).
I used the following openssl command to generate the CSR
openssl req -new -newkey rsa:2048 -nodes -out www_bekwam_biz.csr -keyout www_bekwam_biz.key -subj "/C=US/ST=Maryland/L=Hagerstown/O=Bekwam, Inc/CN=www.bekwam.biz"
I uploaded the text contents of the CSR to Network Solutions, validated the domain via email, and received a ZIP with 3 certificates: the public key and two intermediate certificates.
In the preceding form, paste the public key in “Certificate”, the private key in “Private key”, and a concatenation of intermediate certificates in “Certificate chain”. For my Network Solutions certificate, I pasted the text contents back-to-back from the following files which I downloaded in a zip with the public key.
DV_NetworkSolutionsDVServerCA2.crt
DV_USERTrustRSACertificationAuthority.crt
If successful, you should see a Domains tab like the following.
It’s easy to configure the branding for your Okta login page. This is a convenient facade that replaces the default view and doesn’t involve working with the Authorization Server or client Applications. As such, this is not multi-tenancy. Different brands still work with the same users, groups, and scopes as defined in the Applications > Applications and Security > API screens.